Result
Global-distributed IT-Architectures
Currently, Enterprise Architects are dealing with an international evolving IT-situation combined with rapidly changing external factors. The business IT is coming from a rather decentralized IT-environment and moving towards a more centralized and standardized IT-structure. At the same time, geopolitics are facing a change from a more stable to a fast changing, volatile world, leading to, amongst others, the creation of various regional regulations or laws to protect a country’s data (e.g., sensitive, personal, critical).
For an enterprise, not fulfilling such requirements, this could lead to significant monetary punishments or even a restriction on business relations. Similarly, all political crises, like wars or limited trade relations, have a massive influence on enterprises and, consequently, on their business and enterprise architecture. These external changes cause a forced adaption of original IT concepts towards a more flexible and localized structure.
Mitigating and managing the risks for global IT and data services in a company, requires a clear and comprehensive view and understanding of the requirements, deriving from local regulations and environments. Furthermore, the advantages and disadvantages for a corporate strategy, positioning itself on the scale of “centralization” vs. “decentralization” need to be carefully evaluated to find the best approach for the respective company. A six-step approach supports the right level of adaptation of the enterprise architecture to regional/local and geopolitical requirements.
1. Enterprise Strategy:
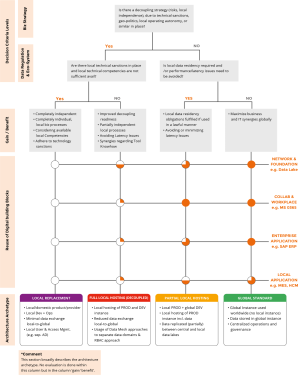
The Enterprise strategy provides the guideline for goals and content of all business activities. A strategy for localization and decoupling means a most sufficient adaptation to the specific requirements of a country. In general, there a many different possible ways to answer to IT relevant requirements. Companies should orientate towards strategic elements to be prepared for current and future requirements. The figure shows four major IT landscape dimensions, which are mainly affected by specific local and geopolitical requirements and how these dimensions could be addressed with concrete IT decoupling scenarios.
2. Regional & local requirements and peculiarities:
Stricter and more volatile regulatory requirements and geopolitical developments limit the strategic options for internationally operating enterprises. Companies need to permanently react on changing conditions and external requirements (e.g. local legal obligations). Therefore, it is necessary to have the local requirements situation always available and transparent. This is the prerequisite to be able to prepare and react on observed changes. A proven methodology is to observe the environment by the principle of a "compliance radar", investigating not only the current local situation but also forecasting the upcoming changes.
3. As-Is EA:
Internationally operating enterprises build on existing architectures, tailored to the enterprise strategy. Transparency on the given IT and data landscape must provide sufficient level of detail and quality on EA data. The underlying EA metamodel must contain the required set of information, e.g. data hosting location, level of data sensitivity, cross-border data transfer information, business criticality of applications, manufacturer of used technologies. To achieve this, a set of standardized EA artefacts (standard views), as a common way for communicating architecture content should be established and constantly used to create and preserve architecture transparency.
4. Compliance/ risk assessment:
During an As-Is/To-Be comparison, existing gaps and potential risks and deficiencies are analyzed and assessed. In the rather prominent and comparatively complex case of China, a combination of local legislation and regulations like China’s Cyber Security Law (CSL), its data-related regulatory rules like the Data Security Law (DSL) and the Personal Information Protection Law (PIPL) require organizations to assess their IT landscape to identify which regulatory risks might exist. An assessment of the potential risks coming from these regulations can be supported from the information stored in an EA repository.
5. Optimized EA Solutions:
Building on existing gaps, optimized EA structures, and solutions could be designed. The whitepaper provides some concrete examples of how the CBA Lab members cope with the challenge of designing the globally distributed architectures in a right way. Examples cover the architecture domains, ERP, Data Lake, IT Network, API Management, eCommerce and Social CRM.
6. EA Governance:
The whitepaper provides a sample set of instruments for stakeholders in the enterprise to find the optimal EA decoupling scenario for a Global-distributed Architecture, based on the given set of requirements and preconditions. The evaluation approach for the appropriate EA scenario should have a reproducible character, in that the same input parameter leads to always the same scenario or architecture archetype. In this whitepaper, we elaborated a decision tree supporting the scenario selection.
 Deutsch
Deutsch  English
English